What is Ransomware and How Does it Work?
If you own a business and follow the news at all, you’ve probably been aware of stories of businesses of all sizes becoming targets of ransomware attacks in the last few years. The uptick in ransomware attacks is alarming.
And while you hear about the biggest ones that happen to companies and entities like the country of Costa Rica or Toyota, what you don’t hear about are the other 1.7 million estimated ransomware attacks that happen each day.
So you certainly don’t need to be a national government or own a major corporation to be worried about ransomware. In this blog, our goal is to educate you on what ransomware is, how it works, share some recent attacks, and give you an overview of what to do if you do find your business has been targeted by ransomware attackers.
What is Ransomware?
Ransomware is a type of malicious software, or malware, that cybercriminals use to hold your computer files hostage and demand a ransom from you to release them. It’s like a digital kidnapping.
Once ransomware infects a computer or network, it encrypts your files, making them unreadable without an encryption key. The cybercriminals then demand that the business pays them a certain amount of money, usually in cryptocurrency, in exchange for the decryption key to unlock the files.
Ransomware can enter the victim’s computer through various means, such as clicking on a malicious link, opening an infected email attachment, or downloading compromised software. It can affect individuals, businesses, and even entire organizations.
The goal of ransomware is to exploit your fear and urgency to get ransomware victims to pay the ransom quickly. However, it’s important to note that there’s no guarantee that by paying the ransom the cybercriminals will actually unlock your files. So it’s generally recommended not to give in to the ransom demands. Instead seek professional help to remove the ransomware and restore your files from backups, if available. But we’ll go more into that later.
How Does Ransomware Work?
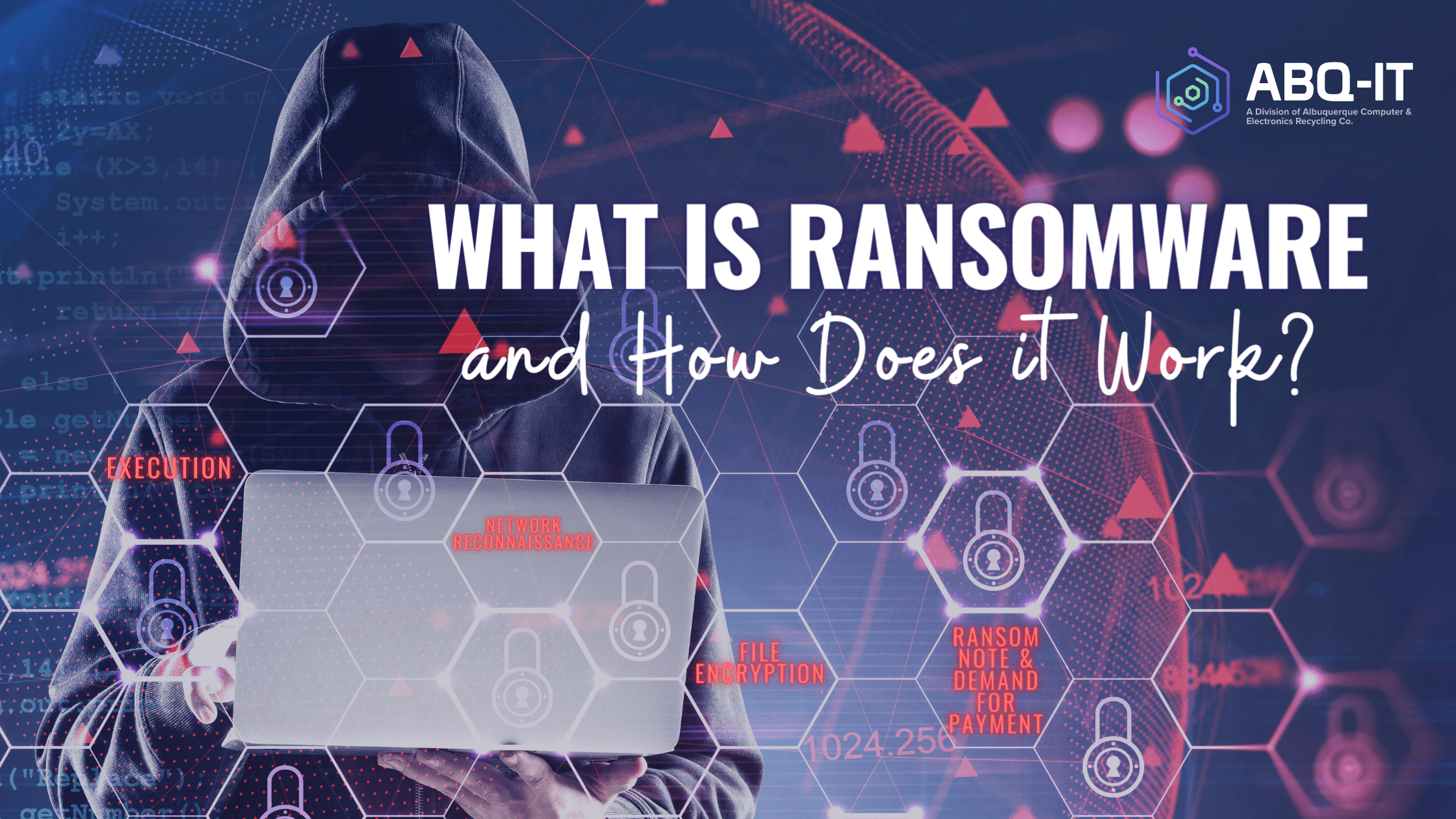
Ransomware typically enters the victim’s computer through one of a few common methods which we will get into a little more in a minute. Once ransomware infiltrates a computer, it typically follows these steps to encrypt files.
Step 1: Execution
The malicious code runs on the victim’s computer, often disguising itself as a legitimate file or process.
Step 2: Network Reconnaissance
Ransomware may scan the network to identify other devices connected to the infected computer. This allows it to spread and encrypt files across multiple devices, such as shared drives or network-attached storage (NAS) devices. This is how entire organizations become infected with ransomware.
Step 3: File Encryption
The ransomware starts encrypting files on the infected computer and, if possible, on connected network devices. It uses strong encryption algorithms to transform the files into an unreadable format. This process may target specific file types, such as documents, images, or databases.
Step 4: Ransom Note & Demand for Payment
After encrypting the files, the ransomware typically displays a message, often in the form of a text file or a full-screen notification. The note informs the victim about the encryption and provides instructions on how to pay the ransom to obtain the decryption key. The amount and payment method vary depending on the ransomware and the attacker’s demands.
It’s worth noting that some sophisticated ransomware strains employ advanced techniques that make it more challenging to decrypt files or trace the cybercriminals.
What Are Some Common Examples of Ransomware?
There are a variety of ways ransomware gets onto a computer, with the most common being through compromised credentials. But there are other ways to install malicious code on a computer.
Phishing Emails
Cybercriminals send emails that appear legitimate and trick users into clicking on a malicious link or opening an infected attachment. Once clicked, the ransomware payload is downloaded and executed on the user’s computer. To learn more about phishing emails and other types of social engineering, check out our recent blog.
Malicious Websites or Downloads
Visiting compromised websites or downloading infected files can expose a computer to ransomware. This can happen when a user unknowingly downloads and installs malicious software or clicks on a deceptive pop-up ad.
Exploiting Software Vulnerabilities
Ransomware can exploit security vulnerabilities in operating systems, web browsers, or other software. If your computer is not updated with the latest security patches, it becomes more susceptible to such attacks. Microsoft Windows historically has been a software ransomware gangs exploit.
Recent High-Profile Ransomware Attacks
Just to give you a few examples of how ransomware attacks play out in real life, we’ll share some recent events, including one that happened right here in Bernalillo County.
Bernalillo County, New Mexico
The attack occurred on January 5, 2022, and caused multiple municipal buildings to shut down. Not only that, but numerous public services in Albuquerque and throughout the county were unavailable for days.
Perhaps what makes this one of the more significant ransomware attacks is that it caused the security cameras and automatic doors to go offline at the Bernalillo County Metropolitan Detention Center. In response, the security team determined that the safest course of action was to keep the inmates in their cells all day, which is a violation of an agreement on inmate conditions.
While it’s not known how the ransomware attack happened, the county responded by greatly increasing its cybersecurity measures, including adding multi-factor authentication for all employee accounts and beginning 24/7 monitoring of the county’s networks.
The County did not pay the ransom demand, and their $2 million insurance policy helped them cover the costs of mitigation and recovery.
Toyota
In February and March of 2022, three apparently unrelated ransomware attacks caused major disruption for Toyota, affecting three of their suppliers, including a malware attack on Bridgestone, shutting down North American production of computer parts.
Throughout the attacks, 14 manufacturing plants had to shut down production for a day, causing a 5% dip in the company’s monthly productivity.
This attack shows just how costly ransomware can be, even if systems are only offline for one day and even if the company doesn’t pay the ransom payment.
There isn’t much information on the details of how these attacks happened or what the result was because Toyota has been pretty tight-lipped about the whole thing. In fact, they’re still calling the halt in production a “system failure.”
At the time of the attacks last year, there was a lot of speculation on whether or not the attacks were related to Japan coming out as a supporter of Ukraine in the war with Russia, giving $100 million in aid.
The attacks highlight that ransomware groups are savvy to the vulnerability of the supply chain. By attacking relatively smaller and more vulnerable companies, hackers are able to make larger companies feel the pain.
CHI Health
CHI Health is a part of one of the biggest non-profit hospital chains in the US, and they fell victim to a ransomware attack in October 2022. It compromised patient data and affected daily operations.
Beyond the annoyance or inefficiency of having to return to patient charting by hand, some patients weren’t able to access the medical equipment they rely on daily due to systems being offline.
The risk to patients might make the CHI Health attack one of the most significant ransomware attacks of 2022, just because it truly was a matter of life and death for some.
One cybersecurity expert, Tony Sabaj, interviewed by local news about the case shared,
“Ransomware actors will go after health care organizations because they’re more apt to pay ransomware attacks to get their systems back online so they can do lifesaving work and not affect patient care.”
As we mentioned before, these are just some of the higher-profile cases of ransomware attacks, but there are hundreds of millions of ransomware attacks that happen each year that don’t hit the news cycle, but still cause significant damage to businesses.
How to Respond to a Ransomware Attack
If your business does get a ransomware infection, it’s important not to panic, slow down, and take the following steps.
- Isolate and disconnect: Quickly finding the infected device is key to preventing the ransomware spreading further. Disconnect infected computers from the internet and other connected devices. This helps contain the impact and protect unaffected systems.
- Notify your IT department or managed service provider: Inform your IT department or managed service provider (MSP) about the attack. Make sure to bring key stakeholders, such as management, legal counsel, and public relations, into the loop so you can have a unified response and decision-making process.
- Report the incident: Contact your local law enforcement agency and report the ransomware attack. Share all the relevant details and any evidence you have. This step helps initiate an investigation and potentially assists in apprehending the attackers.
- Engage cybersecurity professionals: Get assistance from cybersecurity experts who specialize in handling ransomware attacks. They can help assess the situation, identify the ransomware variant, provide guidance on remediation, and assist with data recovery.
- Document evidence: Save evidence related to the attack, like ransom notes, screenshots, and network logs. This information will be valuable for investigations and legal proceedings.
- Determine the scope of the attack: Conduct a thorough analysis to determine which systems, files, and data have been compromised. Assess the potential impact on business operations, critical assets, and customer data. Understanding the scope helps prioritize recovery efforts.
- Restore from backup files: If you have them, restore affected systems and data from secure, unaffected backups. Ensure that backup data is regularly updated, stored securely, and not directly accessible from compromised systems.
- Evaluate decryption options: In some cases, cybersecurity experts or law enforcement agencies may have tools or decryption keys available for certain ransomware variants. Explore these options to potentially recover encrypted files without paying the ransom.
- Communicate with stakeholders: Develop a communication plan to inform employees, customers, and other relevant parties about the incident. Be transparent about the situation, the steps taken to mitigate the impact, and any potential risks they should know about.
- Strengthen security measures: Learn from the incident and enhance your cybersecurity defenses. Implement robust security practices, such as regular software updates, employee training on phishing awareness, strong password policies, and network segmentation.
Remember, it’s generally not recommended to pay ransom payments, since that encourages cybercriminals to keep doing what they’re doing. Plus, there is no guarantee the ransomware perpetrators will provide the decryption key. Instead, focus on proactive measures to prevent future attacks.
Protect Your Business from Ransomware Attacks in 2023
Protect your business from ransomware attacks by being proactive and getting a cybersecurity audit. The professionals at ABQ-IT can help businesses all over the U.S. with ransomware protection.
Between ongoing surveillance, ensuring your data is consistently backed up, antivirus software, firewalls, and education on best practices for cybersecurity, ABQ-IT can help you prevent ransomware and mitigate the damage on any attacks that could sneak their way through. Give us a call at (505)582-6583.

